1. Define the term “Contract”. Discuss the different stages at which communication of Offer and Acceptance completes.
Ans. Section 4 of the Indian Sale of Goods Act of 1930 defines a contract of sale of goods as “a contract whereby the seller transfers or agrees to transfer the property in goods to the buyer for a price”.
A contract of sale includes a sale as well as an agreement to sell. In a sale the property in the goods (i.e. ownership of the goods) passes from the seller to the buyer at the time of the contract of sale. But in an agreement sell, the property in the goods does not pass from the seller to the buyer at the time of contract of sale. It will ass after the expiry of a specified period or after the fulfillment of some condition.
Contract Essentials
When one party agrees to provide goods or services to another party, a contract is made. A contract does not generally have to be in writing to be enforceable. It is, therefore, very easy to make a contract almost without realising it. For instance, if a customer telephones a seller, asks the seller to supply them with a particular type of product and the seller quotes a price which the customer accepts, a contract has been made.
It is very important that everybody involved in the supply of goods or services understands when a contract has been made and what terms govern the contract once it has been made.
To form a contract two elements need to be present: offer and acceptance. Looking at the example above, the offer is to supply the product at the price specified, the acceptance is the agreement by the customer to buy.
There is, in reality, a third element to the contract, namely, certainty. In most cases, this means that the goods or services which form the contract must be certain (i.e. both sides must know precisely what they mean) and the price must be certain. If nothing else is said before the contract is made, all other terms (e.g. delivery date) will be implied.
A contract is made when an offer is accepted, that is, when the bargain is struck. The precise time of making the contract is important because terms of a contract cannot be introduced after this time. Thus, the seller may have standard terms of business - e.g. as to the time when payment is due - but if he does not introduce these to the customer before the contract is made, they are of no relevance.
Satisfactory quality means the quality that a reasonable person would regard as satisfactory taking into account the price and description.
There are now specific matters which should be taken into consideration when determining whether an item is of "satisfactory quality". These include:
• the fitness for the purpose for which the goods are commonly sold;
• appearance and finish;
• freedom from minor defects;
• safety and durability.
Fit for the purpose means they should be fit for the purpose made know at the time of the purchase. A Mini motor car will be fit for the purpose of driving on the road. If however you wanted to use it as an off road vehicle you may not have a claim when you discover it does not perform too well!
"Matching the description" means that the goods should match any picture, packaging or words used to describe them.
If the good are not of satisfactory quality the buyer can get his money back as long as he acts within a reasonable time.
The question of what is a reasonable time has been litigated before the Court on numerous occasions and varies depending upon the nature of the goods.
Essentially it is important that people reject goods swiftly if they are defective and that they thoroughly inspect and test goods at an early stage after purchase. If a minor defect is found the buyer must decide quickly whether to reject the goods and cancel the contract.
Even if the purchaser has lost his rights to reject the goods he can still pursue a claim for damages.
Q. 3. Discuss the impact of Information Technology on Copyrights
Ans
Copyright is a protection that covers published and unpublished literary, scientific and artistic works, whatever the form of expression, provided such works are fixed in a tangible or material form. This means that if you can see it, hear it and/or touch it - it may be protected. If it is an essay, if it is a play, if it is a song, if it is a funky original dance move, if it is a photograph, HTML coding or a computer graphic that can be set on paper, recorded on tape or saved to a hard drive, it may be protected. Copyright laws grant the creator the exclusive right to reproduce, prepare derivative works, distribute, perform and display the work publicly. Exclusive means only the creator of such work, not anybody who has access to it and decides to grab it.
When does Copyright Protection begin, and what is required?
Copyright protection begins when any of the above described work is actually created and fixed in a tangible form.
For example, my brother is a musician and he lives in the United States. When he writes new lyrics, he prints them out on paper, signs his name at the bottom with the Copyright © symbol to show that he is the author, places it in an envelope and mails it to himself without opening it. His copyright begins at the moment he puts his idea in a tangible form by printing the lyrics out on paper. He creates proof when he mails it to himself - the postmark establishes the date of creation. He then registers his copyright with the U.S. Copyright Office which is a requirement in order to sue for monetary damages should a violation of his copyright arise. However, if somebody copies and redistributes his lyrics without permission before his copyright is registered, he still has the right to assert a copyright claim as the true author.
The above applies to digital art and graphics. Open a gif, jpg or png file that you created and look at the properties. It states the date that you saved it to your hard drive as the date of creation. If somebody copies a graphic from your web site I assure you that the date of creation on your copy of the file is earlier than the copy taken off your web site. If that still doesn't feel like enough proof for you, save everything to a floppy disk and mail it to yourself via certified mail. Keep the envelope sealed, wrap it in protective plastic and put it in a safe place.
Somebody once asked if it was "illegal" to place the copyright © symbol next to your name if you have not registered your copyright. Unless you have stolen the work from somebody else and you are not the true author of the work, it is not illegal to place the copyright © symbol next to your name - it is your right to do so.
The proper way to place a copyright notice is as follows: Copyright © (first date of creation) (name of owner). Like this: Copyright © 2003 John Smith.
Copyrights and the Internet.
Public domain - not! When visiting a web site, it is so easy to click and save with a mouse button when one sees a graphic image that one likes, or to view the source code and copy part of or all of the HTML coding because one "likes the way this or that was done" or one "wants a similar layout", or to copy original writings because "that person expresses this or that so well". The general (and incorrect) notion is that anything that is on the internet is public domain and may be taken without permission from the creator/owner. Some people actually think (incorrectly) that just because bits of web pages may be stored in one's cache, or because certain browsers allow one to do "file save as" moves or anything similar one may use such material as one wishes. This is false.
Just because your driveway is not inside of your house, is it in the public domain? Does that give anybody off the street the right to stay on your driveway without your permission, even if they can see it from the street, or easily access it? The same basic principle applies to material published on the internet. Material found on the web may be copied freely only if the information is created by the (i) federal government, (ii) if the copyright has expired or (iii) the copyright has been abandoned by the holder. Therefore, "internet" and "public domain" are not synonymous. Any work published on the internet is not automatically placed it in the public domain, unless the material in question complies with one or more of the characteristics mentioned.
Material provided by others and used with permission. Midis, graphic images (including web graphics, photos, logos and other digital art), writings, text, HTML, javascripts or other material that you are given permission to use or display on your web site does not entitle you to claim copyright to the material in question. Permission to use someone else's material does not make you the rightful owner or holder.
The copyright notice at the bottom of a website only pertains to the content that one has actually created, not to what was created by another and is being used with permission. Owner's terms may vary, but it is always best to include text on the same page where the material on loan is being used to specify who the real owner is, and that it is being used with permission. To an extent, this would protect you as well as the appropriate owner as it would be notifying the public that the material is owned by someone...if you failed to properly protect someone else's work that you are using and it turns out that someone else swiped it due to your misuse or negligence you may be subjecting yourself to a claim.
"Free" web graphics and linking images. Graphic images provided by "free" or "linkware" graphics sites are not public domain. These images, although provided to you for "free" (no $), are not being given to you in ownership. You are being allowed to use them if you comply with the owner's terms and conditions, so make sure that you comply with them in full when you use or display the graphics in question. If the owner says "don't alter it", don't alter it. If the owner says, "only use for your personal homepage," only use it for your personal homepage. The same applies to linking images or logos. They are still copyrighted by the owner and are usually only to be used for links to the owner's web site. Again, in these cases the © symbol at the bottom of your web site only pertains to the content that you yourself created, not to the logos provided to you for links or the "free" graphics loaned to you to decorate your web pages.
Fonts and Dingbats. Some believe that typography may not be protected by a copyright, and once created becomes public domain. Why can't it be protected by a copyright? Because it is so easily downloadable and distributable? Because others use it as a tool to create new means of expression and art forms? I am of the opinion that original fonts and dingbats are a means of expression that may be fixed to a tangible medium when created, and hence become protected by a copyright owned by the creator. The creative process plays an important role. Scanned designs converted into fonts and/or dingbats, or reduplication/refabrication/alteration of existing ones are not original designs, and do not entitle the individual to claim ownership. Fonts and dingbats created point by point, drawn from scratch or through similar means are copyrighted by the author. If this weren't the case, original font and dingbat creators would not be able to legally sell their creations or establish terms and conditions for use. Opinions regarding this particular issue vary but this is what I personally affirm.
Further answers to questions regarding copyrights of typography may be found at Sue Ralston's Ring-a-Ding FAQ's at Web of Dreams.
What about public domain and/or royalty-free stuff? Midis, graphic images (including web graphics, photos, logos and other digital art), writings, text, HTML, javascripts or other material in the public domain does not grant you the right to claim copyright to it just because you find it and use it. Your copyright statement only refers to the content that you created yourself, not to the public domain material you're using. In this case, you cannot complain if you find the same material on someone else's site.
Word of caution: If you are not 100% sure that the material is in the public domain (sometimes "free sites" offer copyrighted material), do not use it. Placing little disclaimers that read, "if you find anything on this page that belongs to someone else contact me" or "if you feel that I may be violating someone's copyright please let me know" just don't cut it and are even irresponsible. You may be violating somebody's copyright.
Hey - everyone knows that HTML coding and webpage layouts cannot be copyrighted! Based upon what? I am of the opinion that a webpage layout may be copyrighted if it is actually written and/or designed by the author and has been fixed in a tangible medium by being saved to a hard drive.
If you wanted, you could put your HTML into a text file and print it out, couldn't you? Doesn't that make it tangible - something you can read or look at? However, this only applies if one actually wrote the HTML coding and designed the web page layout by oneself (even if one uses an HTML editor). If one copies and pastes HTML from one web page into another one may not claim copyright. It is not an original work, and may even be construed as copyright infringement.
There is one thing that must be clarified, though. If you see a certain page layout and like the way it looks, you could "legally" reproduce something similar if you write the coding all by yourself without copying any of the source code from the original page. The actual intangible idea may not be copyrighted. What is copyrighted is the tangible result of the idea, which would be the layout written out in HTML coding and saved to a hard drive. That means no copying and pasting of another person's source code.
Here is an example: If I have the "idea" to make a webpage about roses, that idea cannot be copyrighted because an idea itself will always be intangible. What is copyrighted are the tangible works I produce of the idea. These would be the descriptions I write, my photos of roses, and the HTML coding I created to design the page layout - all saved in my computer's hard drive. All of that is my idea fixed in a tangible medium and that is protected by my copyright. However, somebody else could come along, learn of the idea I had to create a web page about roses, and create a web page about roses as well - provided such person wrote his/her OWN words, used his/her OWN photos, and wrote his/her OWN HTML coding to design the page. Further, if such person was "inspired" by my web page layout, and decided to do something similar (similar - not identical), he or she could do that if the HTML were written entirely by this person without any copying or pasting. All of that is legal, whether it is imaginative and creative, well, that is something else. Now, if this person came along, saw my web page on roses, liked the way I did it and then copied and pasted my HTML into his or her own web page without my permission, that is copyright infringement, even if he or she deleted certain things and inserted his or her OWN words and his or her OWN photos. Yes, even if he or she did NOT have a web page about roses, but about something entirely different. That is because my page layout was written out in HTML and set in a fixed form, and the fixed form is what was copied without my permission.
What if I take someone else's writings, text, HTML or graphic image and change it around to suit my needs? I own the "new" version, right? If you did any of that with the original owner's permission, and according to his/her terms and conditions than you own the "new" version. If not you may be committing copyright infringement and/or plagiarism.
What if I translate your copyright page into another language? I bet I don't need your permission, and I own the "new" work! The Berne Convention states, "Authors of literary and artistic works protected by this Convention shall enjoy the exclusive right of making and of authorizing the translation of their works throughout the term of protection of their rights in the original works."
That means that you need my permission to translate this page into another language. Also, there is not really a "new" work. You have merely translated an existing work into another language. You own the full copyright to the translation only, and even if you have my permission to translate it, you still need to credit me within the translation as author of the original work.
Hot-linking and Spider Harvesting. Hot-linking, or linking directly to another website's images and/or spider-harvesting (robots programmed to index pages and pull images onto another server) is not only bandwith theft, but may also be construed as copyright infringement in some cases. The images that are hot-linked are reproduced in the website that is performing the direct linking and/or spider-harvesting as an unauthorized derivative work, or may be giving the impression that the owner of the images is the one who is hot-linking. Either constitute a violation of the real owner's copyright.
ease navigation within a site is perfectly acceptable. However, it is not acceptable to "lock" or "trap" other web sites or pages in one's frames. Firstly, it's extremely rude. If your site content is interesting enough you shouldn't worry about visitors returning to your site if they leave momentarily through an outside link. Secondly, I am of the opinion that showing someone else's web page through the use of frames may be construed as copyright infringement in some cases. For example, if I pull someone else's page with original poetry on it into my own site through the use of frames may mislead others to believe that I am the author of the poetry. When one intentionally or unintentionally gives another the impression that one is the creator of someone else's work, that is a violation of the real owner's copyright
Q. 4. Explain how Encryption works.
Ans. The incredible growth of the Internet has excited businesses and consumers alike with its promise of changing the way we live and work. But a major concern has been just how secure the Internet is, especially when you're sending sensitive information through it.
Let's face it, there's a whole lot of information that we don't want other people to see, such as:
• Credit-card information
• Social Security numbers
• Private correspondence
• Personal details
• Sensitive company information
• Bank-account information
Information security is provided on computers and over the Internet by a variety of methods. A simple but straightforward security method is to only keep sensitive information on removable storage media like floppy disks. But the most popular forms of security all rely on encryption, the process of encoding information in such a way that only the person (or computer) with the key can decode it.
In this article, you will learn about encryption and authentication. You will also learn about public-key and symmetric-key systems, as well as hash algorithms.
Encryption Systems
Computer encryption is based on the science of cryptography, which has been used throughout history. Before the digital age, the biggest users of cryptography were governments, particularly for military purposes. The existence of coded messages has been verified as far back as the Roman Empire. But most forms of cryptography in use these days rely on computers, simply because a human-based code is too easy for a computer to crack.
Most computer encryption systems belong in one of two categories:
• Symmetric-key encryption
• Public-key encryption
In the following sections, you'll learn about each of these systems.
Symmetric Key
In symmetric-key encryption, each computer has a secret key (code) that it can use to encrypt a packet of information before it is sent over the network to another computer. Symmetric-key requires that you know which computers will be talking to each other so you can install the key on each one. Symmetric-key encryption is essentially the same as a secret code that each of the two computers must know in order to decode the information. The code provides the key to decoding the message. Think of it like this: You create a coded message to send to a friend in which each letter is substituted with the letter that is two down from it in the alphabet. So "A" becomes "C," and "B" becomes "D". You have already told a trusted friend that the code is "Shift by 2". Your friend gets the message and decodes it. Anyone else who sees the message will see only nonsense.
Public Key
Public-key encryption uses a combination of a private key and a public key. The private key is known only to your computer, while the public key is given by your computer to any computer that wants to communicate securely with it. To decode an encrypted message, a computer must use the public key, provided by the originating computer, and its own private key. A very popular public-key encryption utility is called Pretty Good Privacy (PGP), which allows you to encrypt almost anything. You can find out more about PGP at the PGP site.
To implement public-key encryption on a large scale, such as a secure Web server might need, requires a different approach. This is where digital certificates come in. A digital certificate is basically a bit of information that says that the Web server is trusted by an independent source known as a certificate authority. The certificate authority acts as a middleman that both computers trust. It confirms that each computer is in fact who it says it is, and then provides the public keys of each computer to the other.
Public Key: SSL
A popular implementation of public-key encryption is the Secure Sockets Layer (SSL). Originally developed by Netscape, SSL is an Internet security protocol used by Internet browsers and Web servers to transmit sensitive information. SSL has become part of an overall security protocol known as Transport Layer Security (TLS).

Look for the "s" after "http" in the address whenever you are about to enter sensitive information, such as a credit-card number, into a form on a Web site.
In your browser, you can tell when you are using a secure protocol, such as TLS, in a couple of different ways. You will notice that the "http" in the address line is replaced with "https," and you should see a small padlock in the status bar at the bottom of the browser window.
The padlock symbol lets you know that you are using encryption.
Public-key encryption takes a lot of computing, so most systems use a combination of public-key and symmetry. When two computers initiate a secure session, one computer creates a symmetric key and sends it to the other computer using public-key encryption. The two computers can then communicate using symmetric-key encryption. Once the session is finished, each computer discards the symmetric key used for that session. Any additional sessions require that a new symmetric key be created, and the process is repeated.
Hashing Algorithms
The key in public-key encryption is based on a hash value. This is a value that is computed from a base input number using a hashing algorithm. Essentially, the hash value is a summary of the original value. The important thing about a hash value is that it is nearly impossible to derive the original input number without knowing the data used to create the hash value. Here's a simple example:
Input number Hashing algorithm Hash value
10,667 Input # x 143 1,525,381
You can see how hard it would be to determine that the value 1,525,381 came from the multiplication of 10,667 and 143. But if you knew that the multiplier was 143, then it would be very easy to calculate the value 10,667. Public-key encryption is actually much more complex than this example, but that is the basic idea.
Public keys generally use complex algorithms and very large hash values for encrypting, including 40-bit or even 128-bit numbers. A 128-bit number has a possible 2128 or 3,402,823,669,209,384,634,633,746,074,300,000,000,000,000,000,000,000,000,000,000,000,000 different combinations! This would be like trying to find one particular grain of sand in the Sahara Desert.
Authentication
As stated earlier, encryption is the process of taking all of the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Another process, authentication, is used to verify that the information comes from a trusted source. Basically, if information is "authentic," you know who created it and you know that it has not been altered in any way since that person created it. These two processes, encryption and authentication, work hand-in-hand to create a secure environment.
There are several ways to authenticate a person or information on a computer:
• Password - The use of a user name and password provides the most common form of authentication. You enter your name and password when prompted by the computer. It checks the pair against a secure file to confirm. If either the name or the password does not match, then you are not allowed further access.
• Pass cards - These cards can range from a simple card with a magnetic strip, similar to a credit card, to sophisticated smart cards that have an embedded computer chip.
• Digital signatures - A digital signature is basically a way to ensure that an electronic document (e-mail, spreadsheet, text file) is authentic. The Digital Signature Standard (DSS) is based on a type of public-key encryption method that uses the Digital Signature Algorithm (DSA). DSS is the format for digital signatures that has been endorsed by the U.S. government. The DSA algorithm consists of a private key, known only by the originator of the document (the signer), and a public key. The public key has four parts, which you can learn more about at this page. If anything at all is changed in the document after the digital signature is attached to it, it changes the value that the digital signature compares to, rendering the signature invalid.
Recently, more sophisticated forms of authentication have begun to show up on home and office computer systems. Most of these new systems use some form of biometrics for authentication. Biometrics uses biological information to verify identity. Biometric authentication methods include:
• Fingerprint scan
• Retina scan
• Face scan
• Voice identification
Checking for Corruption
Another secure-computing need is to ensure that the data has not been corrupted during transmission or encryption. There are a couple of popular ways to do this:
• Checksum - Probably one of the oldest methods of ensuring that data is correct, checksums also provide a form of authentication because an invalid checksum suggests that the data has been compromised in some fashion. A checksum is determined in one of two ways. Let's say the checksum of a packet is 1 byte long. A byte is made up of 8 bits, and each bit can be in one of two states, leading to a total of 256 (28 ) possible combinations. Since the first combination equals zero, a byte can have a maximum value of 255.
If the sum of the other bytes in the packet is 255 or less, then the checksum contains that exact value.
If the sum of the other bytes is more than 255, then the checksum is the remainder of the total value after it has been divided by 256.
Let's look at a checksum example:
Byte 1 Byte 2 Byte 3 Byte 4 Byte 5 Byte 6 Byte 7 Byte 8 Total Checksum
212 232 54 135 244 15 179 80 1,151 127
• 1,151 / 256 = 4.496 (round to 4)
• 4 x 256 = 1,024
• 1,151 - 1,024 = 127
• Cyclic Redundancy Check (CRC) - CRCs are similar in concept to checksums, but they use polynomial division to determine the value of the CRC, which is usually 16 or 32 bits in length. The good thing about CRC is that it is very accurate. If a single bit is incorrect, the CRC value will not match up. Both checksum and CRC are good for preventing random errors in transmission but provide little protection from an intentional attack on your data. Symmetric- and public-key encryption techniques are much more secure.
All of these various processes combine to provide you with the tools you need to ensure that the information you send or receive over the Internet is secure. In fact, sending information over a computer network is often much more secure than sending it any other way. Phones, especially cordless phones, are susceptible to eavesdropping, particularly by unscrupulous people with radio scanners. Traditional mail and other physical mediums often pass through numerous hands on the way to their destination, increasing the possibility of corruption. Understanding encryption, and simply making sure that any sensitive information you send over the Internet is secure (remember the "https" and padlock symbol), can provide you with greater peace of mind.
Q. 6. Describe the different types of e-commerce security policies, applications and technologies, which are currently in use.
Ans. Corporate networks are built assuming certain levels of trust in how the information passing through them is accessed and used. When they're hooked into public networks, like the Internet, a safer -- and more intelligent route -- leads security administrators to trust no one on the outside.
In this page, we will examine fire wall that protects network and system vulnerabilities on systems attached to the Internet, as well as for private networks.
To help answer any questions you may have about where fire wall is needed and used, this on line tutorial will explain security technologies used to defend against attacks initiated from both within and without an organization. The on line tutorial will examine the pieces of the security puzzle to see how to best fit them together for effective defenses and coverage. In the page, we'll explore several security methods that are used wherever the Internet and corporate networks intersect. These include the uses of:
• Routers
• Firewalls
• Intrusion Detection Systems (IDSs)
• Vunerability Assessment Tools (Scanners, etc.)
• Basic Security Infrastructures
Figure 1 illustrates the basic design for a secure network infrastructure. As you see, the infrastructure relies upon layers of devices that serve specific purposes, and provide multiple barriers of security that protect, detect, and respond to network attacks, often in real time.
Figure 1 : A Basic Network Security Model
Routers
A router is a network traffic-managing device that sits in between sub-networks and routes traffic intended for, or emanating from, the segments to which it's attached. Naturally, this makes them sensible places to implement packet filtering rules, based on your security polices that you've already developed for the routing of network traffic.
Packet Filtering
Straight Packet Filtering mechanisms allow communication originating from one side or the other. To enable two-way traffic, you must specify a rule for each direction. Packet filtering firewalls identify and control traffic by examining the source, destination and port
What Is A Firewall?
A firewall insulates a private network from a public network using carefully established controls on the types of request they will route through to the private network for processing and fulfillment. For example, an HTTP request for a public Web page will be honored, whereas an FTP request to a host behind the firewall may be dishonored. Firewalls typically run monitoring software to detect and thwart external attacks on the site, and are needed to protect internal corporate networks. Firewalls appear primarily in two flavors; application level gateways and proxy servers. Other uses of firewalls include technologies such as Virtual Private Networks that use the Internet to tunnel private traffic without the fear of exposure
Defining firewalls
A slightly more specific definition of a firewall comes from William Cheswick and Steven Bellovin, two engineers with AT&T who wrote the classic Firewalls and Internet Security (Addison Wesley, 1994). They based the book on their experience developing a firewall to protect AT&T connections to the Internet. Cheswick and Bellovin define a firewall as a collection of components or a system placed between two networks and possessing the following properties:
* All traffic from inside to outside, and vice-versa, must pass through it;
* Only authorized traffic, as defined by the local security policy, is allowed to pass through it; and
* The system itself is highly resistant to penetration.
Put simply, a firewall is a mechanism used to protect a trusted network from an untrusted network, usually while still allowing traffic between the two. Typically, the two networks in question are an organization's internal (trusted) network and the (untrusted) Internet. However, nothing in the definition of a firewall ties the concept to the Internet. We traditionally define the Internet as the worldwide network of networks that uses TCP/IP for communications. We define an internet as any connected set of networks. Although many firewalls are currently deployed between the Internet and internal networks, there are good reasons for using firewalls in any internet, or intranet, such as a company's WAN. There will be more about this use of firewalls later in this chapter.
Another approach to firewalls views them as both policy and the implementation of that policy in terms of network configuration. Physically, a firewall comprises one or more host systems and routers, plus other security measures such as advanced authentication in place of static passwords. As shown in Figure 1.1, a firewall may consist of several different components, including filters, or screens, that block transmission of certain classes of traffic, and a gateway, which is a machine or set of machines relaying services between the internal and external networks by means of proxy applications. The intermediate area occupied by the gateway we often refer to as the demilitarized zone (DMZ). These terms will all be explained in more detail, starting with traffic.
Figure 1.1: Basic firewall schematic (filters, gateway and DMZ)
Internetwork Traffic
When we say that all traffic from inside to outside and vice-versa, must pass through a firewall, we refer to data transported by the TCP/IP protocol suite. Figure 1.2 illustrates a diagram of TCP/IP, showing the way the protocol is layered and the manner in which addresses are used. To control TCP/IP traffic, one must gain a solid understanding of how it is structured.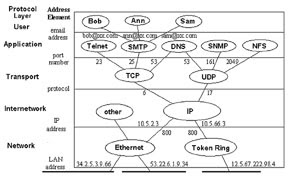
Figure 1.2: Diagram of TCP/IP, showing protocol layers and addressing
A protocol is a formal description of messages to be exchanged and rules to be followed in order for two or more systems to exchange information in a manner that both parties will understand . The TCP/IP protocol suite, officially referred to as the Internet Protocol Suite in Internet standards documents, gets its name from its two most important protocols, TCP and IP. Network applications present data to TCP, the Transmission Control Protocol. TCP divides the data into chunks, called packets, and gives each one a number. These packets could represent text, graphics, sound or video--anything digital that the network can transmit. The sequence numbers help to ensure that the packets can be reassembled correctly at the receiving end. Thus, each packet consists of content, or data, and the information that the protocol needs to do its work, called the protocol header.
TCP then presents the data to the Internet Protocol, or IP, the purpose of which is to provide basic host-to-host communication. IP attaches to the packet, in a protocol header, the address from which the data comes and the address of the system to which it is going. IP is technically referred to as an unreliable datagram service. In this context, the rather alarming term "unreliable" simply means that upper-level protocols should not depend upon IP to deliver the packet every time. IP always does its best to make the delivery to the requested destination host, but if it fails for any reason, it just drops the packet.
This is where the higher-level protocol, TCP, comes in. TCP uses the sequence numbers to reassemble the packets in the right order and request re-transmission of any packets that got lost along the way. It can do this even if some of the packets take different routes to reach their destination, which makes the combination of TCP/IP a very reliable protocol.
TCP uses another piece of information to make ensure that the data reaches the right application when it arrives at a system. This is the port number, lying within the range 1 to 65535. The number does not represent a physical port, like the serial port to which a modem or mouse might be attached, but is more like a regional memory address. Ports 1 to 1,023 are reserved for server applications, although servers can use higher port numbers as well. Higher port numbers are dynamically assigned to client applications as needed. Some applications use standard port numbers; for example, an FTP program will connect to port 21 on the FTP server. Thus, data to be transmitted by TCP/IP has a port from which it is coming and a port to which it is going, plus an IP source and destination address. Firewalls can use these addresses to control the flow of information.
For more about TCP/IP basics, I recommend Intranet and Internet Firewall Strategies by Edward Amoroso and Ronald Sharp, (Ziff Davis Press, 1996). Like Cheswick and Bellovin, Amoroso and Sharp were engineers at AT&T Labs, but whereas Cheswick and Bellovin developed a firewall to protect AT&T from the outside, Amoroso and Sharp developed a trademarked internal firewall, called CWTG or Computer Watch Trusted Gateway. For more advanced reading on TCP/IP we recommend TCP/IP Tutorial and Technical Overview, (5th Edition, Prentice Hall, 1995) by Eamon Murphy, Steve Hayes and Matthias Enders, a trio of IBM engineers.
Firewalls as Filters
When TCP/IP sends data packets on their merry way, the packets seldom go straight from the host system that generated them to the client that requested them. Along the way they normally pass through one or more routers. In this, TCP/IP transmissions differ from LAN communications, which broadcast over a shared wire.
To look at how TCP/IP routes packets, and how this allows sites to filter for security, let us first examine old-fashioned LAN communications. Suppose five PCs reside on a LAN. If PC #2 wants to send some data to PC #4, it shouts out over the network and hopes that PC #4 hears it. The other three systems on the same wire will also hear the same data. This is true of both Ethernet and Token Ring, the two most widely used LAN protocols. This method of communication, in which a number of computers share the same wiring, increases efficiency, limits distance and scope. It also limits the number of computers that can talk on the same wire.
Early efforts to enable computers to communicate with each other over long distances used telephone lines and switches to connect calls from one specific computer to another in a remote location (the X.25 protocol was developed for this). A connection between two computers might pass through several switches until it reached its final destination. When LANs emerged it made sense for all the computers on one LAN to have access to the machine that had access to the remote connection, thus creating a WAN. LAN protocols, however, were incompatible with X.25, and the machine hosting the connection to the WAN tended to get overworked.
Next came a special type of switch called a router, which could take over the work of making external connections, and could also convert LAN protocols, specifically IP, into WAN protocols. Routers have since evolved into specialized computers. The typical router is about the same size as a VCR, although smaller models and rackmounted units for major interconnections have entered the market.
Basically, routers look at the address information in TCP/IP packets and direct them accordingly. Data packets transmitted over the Internet from the Web browser on a PC in Florida to a Web server in Pennsylvania will pass through numerous routers along the way, each of which makes decisions about where to direct the traffic. Figure 1.3 shows the traceroute program in action, listing the path the data takes.
Figure 1.3: The traceroute program shows the path Internet data takes.
Suppose the Web browser is on a PC on a LAN with a PPP connection to an Internet Service Provider (ISP). A router, or a computer acting as a router, will likely direct the packets out from the LAN to the ISP. Routers at the ISP will send the data to a backbone provider, which will route it, often in several hops, to the ISP that serves the machine that hosts the Web site.
Routers make their routing decisions based on tables of data and rules. It is possible to manipulate these rules by means of filters so that, for example, only data from certain addresses may pass through the router. In effect, this turns a router that can filter packets into an access-control device, or firewall. If the router can generate activity logs, this further enhances its value as a security device. We will discuss how this works in more detail in the next chapter.
Firewalls as Gateways
Internet firewalls are often referred to as secure Internet gateways. Like the gates in a medieval walled city, they control access to and from the network.
In firewall parlance, a gateway is a computer that provides relay services between two networks. A firewall may consist of little more than a filtering router as the controlled gateway. Traffic goes to the gateway instead of directly entering the connected network. The gateway machine then passes the data, in accordance with access-control policy, through a filter, to the other network or to another gateway machine connected to the other network.
In some configurations, called dual-homed gateways, one computer containing two network connectors acts as the gateway. Alternatively, a pair of machines can create a miniature network referred to as the DMZ (see Figure 1.4). Typically, the two gateways will have more open communication through the inside filter than the outside gateway has to other internal hosts. The outside filter can be used to protect the gateway from attack, while the inside gateway is used to guard against the consequences of a compromised gateway [Ches94].
Figure 1.4: The use of gateways.
Firewalls as Control Points
By concentrating access control, firewalls become a focal point for the enforcement of security policy. Some firewalls take advantage of this to provide additional security services, including traffic encryption and decryption. In order to communicate in encryption mode, the sending and receiving firewalls must use compatible encrypting systems. Current standards efforts in encryption and key management have begun to allow different manufacturers' firewalls to communicate securely, but these efforts have a ways to go before the customer can assume compatibility. Firewall-to-firewall encryption is thus used for secure communication over the public Internet between known entities with prior arrangement, rather than for any-to-any connections. Nevertheless it is a powerful feature, enabling the creation of virtual private networks (VPN) as a lower-cost alternative to a leased line or a value-added network (VAN).
Verifying the authenticity of system users is another important part of network security, and firewalls can perform sophisticated authentication, using smart cards, tokens and other methods. Firewalls can also protect other external network connections, such as remote dial-in. A company can apply the same traffic-restricting protections, enhanced by authentication.
Internal Firewalls
While the phenomenal growth of Internet connections has understandably focused attention on Internet firewalls, modern business practices continue to underscore the importance of internal firewalls. Mergers, acquisitions, reorganizations, joint ventures and strategic partnerships all place additional strains on security as the scope of the network's reach expands. Someone outside the organization may suddenly need access to some, but not all, internal information. Multiple networks designed by different people, according to different rules, must somehow trust each other. In these circumstances, firewalls play an important role in enforcing access-control policies between networks and protecting trusted networks from those that are untrusted.
Consider a manufacturing company that has, over time, developed separate networks within the sales, marketing, payroll, accounting and production departments. Although users in one department may wish to access certain other networks, it is probably unnecessary and undesirable for all users to have access to all networks. Consequently, when connecting the networks, the organization may choose to limit the connection, either with packet-filtering routers or with a more complex firewall.
In a WAN that must offer any-to-any connectivity, other forms of application-level security can protect sensitive data. However, segregating the networks by means of firewalls greatly reduces many of the risks involved; in particular, firewalls can reduce the threat of internal hacking--that is, unauthorized access by authorized users, a problem that consistently outranks external hacking in information-security surveys. By adding encryption to the services performed by the firewall, a site can create very secure firewall-to-firewall connections. This even enables wide-area networking between remote locations over the Internet. By using authentication mechanisms on the firewall, it is possible to gain a higher level of confidence that persons outside the firewall who request data from inside the firewall--for example, salespersons on the road needing access to an inventory database--are indeed who they claim to be.
Figure 1.5: Firewall to firewall encryption
Firewalls and Policy
Diagrams of the various configurations of filters and gateways help when planning a firewall defense, but the system administrator must not lose sight of the broader definition of a firewall as an implementation of security policy. A firewall is an approach to security; it helps implement a larger security policy that defines the services and access to be permitted. In other words, a firewall is both policy and the implementation of that policy in terms of network configuration, host systems and routers, as well as other security measures such as advanced authentication in place of static passwords.
Types of Network Policy
Two levels of network policy directly influence the design, installation and use of a firewall system. Network service access policy is a higher-level, issue-specific policy that defines those services to be allowed or explicitly denied from the restricted network. This policy also proscribes the way in which these services will be used, and the conditions for exceptions to this policy. Firewall design policy is a lower-level policy that describes how the firewall will actually go about restricting the access and filtering the services as defined in the network service access policy. We will examine both levels of policy in the following sections.
Network Service Access Policy
While focusing on the restriction and use of internetwork services, the network service access policy should also include all other outside network access, including dial-in and SLIP/PPP connections. After all, restrictions upon one type of network service access can often lead users to try others, so those other points of entry must also contain equal protections. For example, if restricting access to the Internet via a firewall prevents users from browsing the Web, some will likely create dial-up PPP connections in order to obtain this service. These non-sanctioned, ad hoc connections are likely to be improperly secured, opening the network to attack.
Network service access policy should stand as an extension of a strong site-security policy and an overall policy regarding the protection of information resources in the organization. This includes everything from document shredders to virus scanners, remote access to removable media tracking.
Typically, a firewall implements one of two general network service access policies: either allowing access to the Internet from the site but allowing no access to the site from the Internet; or allowing some access from the Internet, but only to selected systems such as information servers and e-mail servers. Some firewalls also implement network service access policies that allow certain users access from the Internet to selected internal hosts, but only if necessary and only when combined with advanced authentication.
At the highest level, the overall organizational policy might state the following principles:
1. Information is vital to the economic well being of the organization
2. Every cost-effective effort will be made to ensure the confidentiality, integrity, authenticity, availability and utility of the organization's information.
3. Protecting the confidentiality, integrity and availability of these information resources is a priority and a job responsibility for all employees at all levels of the company.
4. All information-processing facilities belonging to the organization will be used only for authorized purposes.
Below this statement of principles come site-specific policies covering physical access to the property, general access to information systems and specific access to services on those systems. The firewall's network service access policy is formulated at this level.
For a firewall to function as the company desires, the network service access policy should exist prior to the implementation of the firewall. The policy must be realistic and sound. A realistic policy provides a balance between protecting the network from known risks on the one hand and providing users reasonable access to network resources on the other. If a firewall system denies or restricts services, only a strong network service access policy will prevent the firewall's access controls from being modified or circumvented on an ad hoc basis. A sound, management-backed policy can provide this defense against user resistance.
Firewall Design Policy
The firewall design policy is specific to the firewall and defines the rules used to implement the network service access policy. The company must design the policy in relation to, and with full awareness of, issues such as the firewall's capabilities and limitations, and the threats and vulnerabilities associated with TCP/IP. As mentioned earlier, firewalls generally implement one of two basic design policies:
1. Permit any service unless it is expressly denied; or
2. Deny any service unless it is expressly permitted.
Firewalls that implement the first policy (the permissive approach) allow all services to pass into the site by default, with the exception of those services that the service-access policy has identified as disallowed. Firewalls that implement the second policy (the restrictive approach) deny all services by default, but then pass those services that have been identified as allowed. This restrictive second policy follows the classic access model used in all areas of information security.
The permissive first policy is less desirable, since it offers more avenues for circumventing the firewall. With this approach, users could access new services not currently addressed by the policy. For example, they could run denied services at non-standard TCP/UDP ports that are not specifically mentioned by the policy.
This is where firewall design comes in. Certain firewalls can implement either a permissive or a restrictive design policy. A company can also choose to locate those systems requiring services that should not be passed through the firewall on screened subnets, separated from other site systems. Some use this approach for Web servers, which are partially shielded by packet filtering but are not sheltered behind the firewall. (If the Web server calls information from, or feeds data to, internal database systems, then that connection between the Web server and the internal machines should be well protected.)
Saturday, May 16, 2009
MI 14 – 01 E-BUSINESS AND IT LAW
Posted by Shopperix Mall at 8:25 PM
Labels: MI 14 – 01 E-BUSINESS AND IT LAW
Subscribe to:
Post Comments (Atom)



1 Comment:
I read this article. Generally i got domain name host to city converting through domain-host-converting. But after reading this article, i came to know about the encryption process which i had doubt on this topic. Now its clear. Thanks for this article.
Post a Comment